You can find more exciting topics around data security in the COREDINATE Blog.
Security Haller
- For years, Ulrike Haller has been running the security company
- A convinced COREDINATE customer for at least as long
- The new update 8.4.5 offers new, exciting possibilities
Used COREDINATE features
- Data security
The initial situation
Ulrike Haller has been successfully running her security company Security Haller for years. She has been a convinced customer of COREDINATE for at least as long. The innovative assistance system helps her and her team to optimize the company processes efficiently and it facilitates the daily work enormously for all parties involved – from the security staff to the accounting department to the customers.
As a customer of COREDINATE, Ulrike Haller is regularly informed about news, like in the last newsletter, which informed about the new update to version 8.4.5. It talks about 2-factor authentication, which now makes COREDINATE even more secure. Ulrike Haller passes on the news to her employees from the infrastructure and asks them to make the innovations available to the employees immediately.
Everyday work with COREDINATE
Heiko Schilling, an employee in Security Haller's infrastructure, welcomes the introduction of 2-factor authentication at COREDINATE. Although the system has never shown any major security gaps so far, additional protection does not hurt, according to Heiko Schilling's attitude. In doing so, he follows the common recommendation of the German Federal Office for Information Security, which has long recommended using 2-factor authentication for all web services where it is possible.
When introducing 2-factor authentication, Heiko Schilling doesn't even need the assistance of support. Instead, all he has to do is collect the duty cell phones of Security Haller's security staff piece by piece and set up the new feature.
Data security
2-factor authentication – also known as two-factor authentication – increases security when logging into a system by combining two components that act independently of each other, such as the system to be used and an additional authorization app to prove the user's identification.
In this way, Heiko Schilling can counteract the well-known problem that colleagues either use passwords that are too weak or only one password for all web applications. With 2-factor authentication, he can mitigate the risk of these passwords being intercepted by third parties.
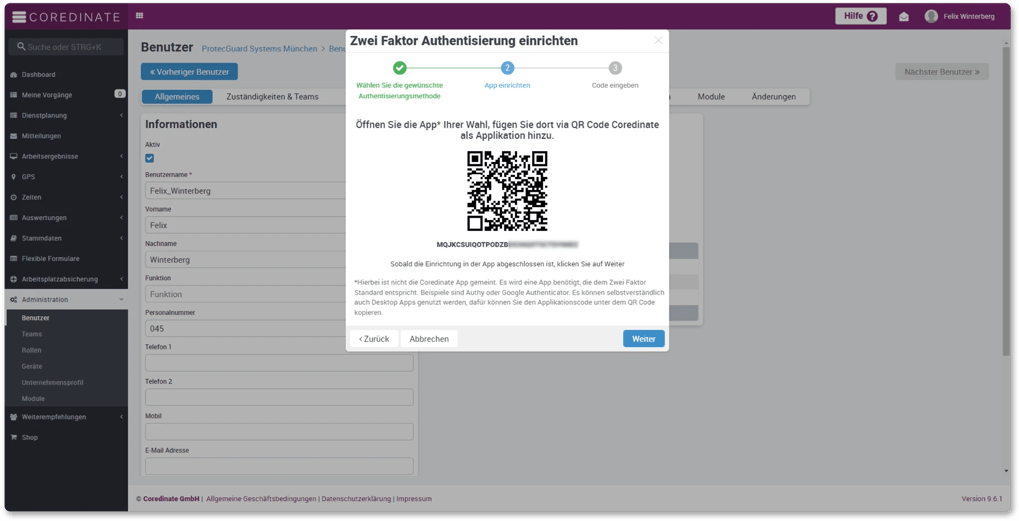
To use 2-factor authentication, Heiko Schilling first has to install an additional app for proof of identification on his colleagues' work cell phones. He uses Google Authenticator for this purpose.
After the setup, all users of COREDINATE will now be asked for an additional code when logging in to prove their identity. They can read this code from Google Authenticator.
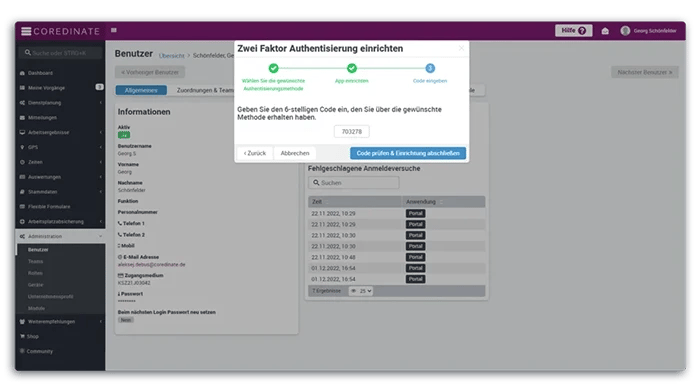
After entering the code in COREDINATE, the user has successfully logged into the system through the additionally secured login and can use it as usual. The code, which is generated from the identification app, changes regularly after a few minutes and can therefore not be used by third parties.
For Ulrike Haller, the introduction of 2-factor authentication means additional protection for company data and the data of her customers, and thus offers her an additional quality feature with which she can promote her work.
You are not yet using the COREDINATE® guard control system? Then it's time to put our test set through its paces for 14 days free of charge and without obligation.
